I had a job interview with a large CDN and learned a new trick. Well, a new wrinkle on an old behavior.
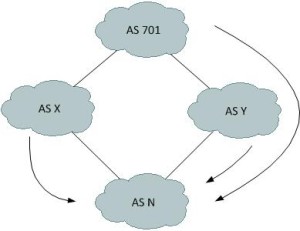
AS N represents the CDN, while AS X and Y are transit providers. Let’s say there is a large eyeball network who refuses to peer with you (AS 701 for the sake of argument). How can you influence the flow of traffic from AS 701 such that they only use AS Y and not AS X?
Typically this would be accomplished via the use of communities with your transit provider. Most transit providers support internal communities allowing the addition of AS prepends toward specific peers, but that is dependent on the provider’s policy framework. Another option is the use of the no-export community, but again this depends on the provider’s implementation.
Instead of relying on communities, you could inject AS 701 into the path list for prefixes advertised toward AS X. When AS X advertises the routes toward AS 701, they will be rejected due to BGP’s AS path loop prevention mechanism. This technique is known as AS path poisoning, and is somewhat difficult to detect via normal troubleshooting since you can’t check the RIB.
Cisco boxes will log an error of the form:
%BGP% Neighbor A.B.C.D recv bogus route : AS loop
On Juniper routers run the following command to view the discarded routes:
show route hidden aspath-regex .*Your-AS.*